This page contains some highlights from the lecture and lab notes I’ve made for students in the past. Feel free to email me for more information on any of these.
NETWORK SECURITY
Cryptography Review
These notes are a quick list of cryptography definitions that we use in our network security class.
(Taken mostly from ‘Introduction to Modern Cryptography’ by Jonathan Katz and Yehuda Lindell)

NETWORK SECURITY
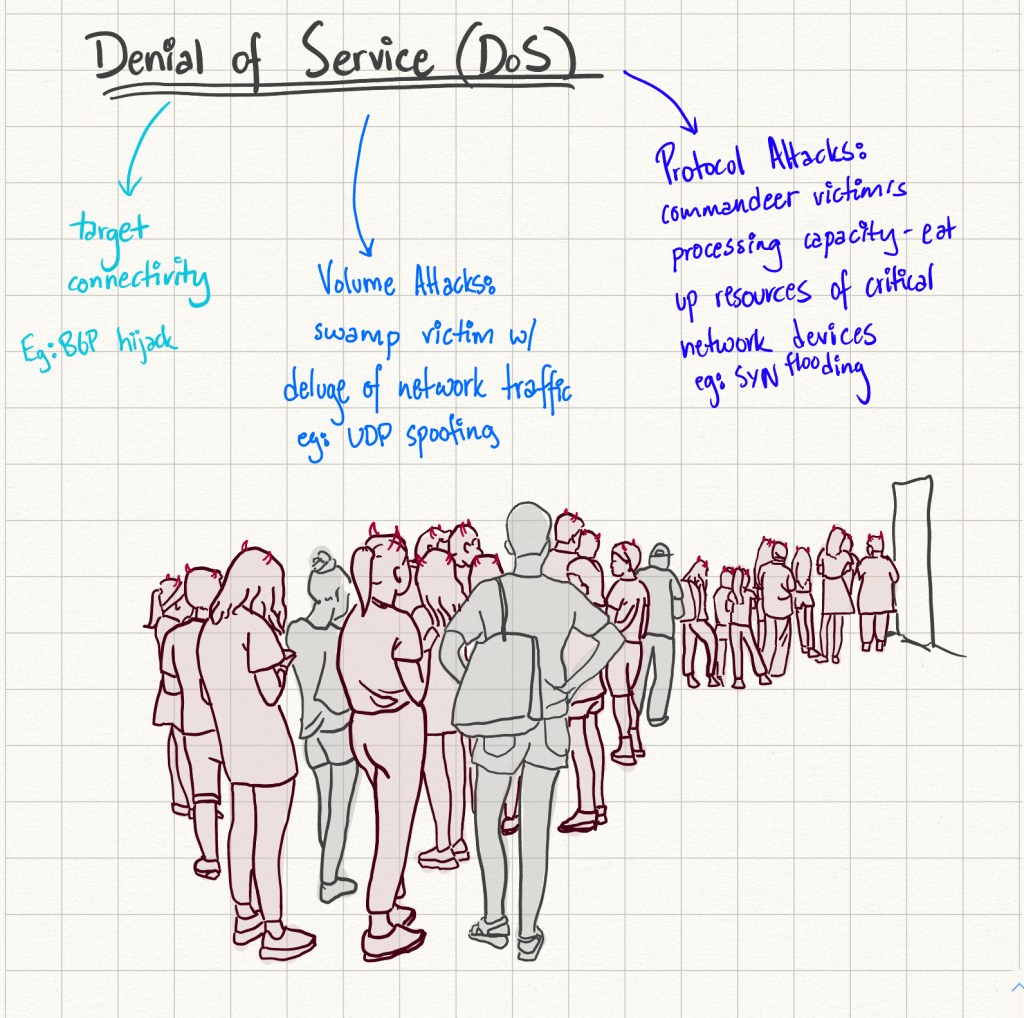
Denial of Service
NETWORK SECURITY
Protecting Metadata 1: Mixnets


NETWORK SECURITY
Protecting Metadata 2: Tor
NETWORK SECURITY
The Signal Architecture
I have extensive notes from the lectures I’ve taught on secure messaging and the Signal architecture. (Which makes it unclear what exactly to link here for download.)
Email me if you’d like my notes or if you’d like to talk about teaching lectures on this protocol and the concepts behind it! 🙂
